The Remote Access Trojan
A remote access trojan(RAT) is one of the scarier and common types of malware to be infected with. Anyone with basic computer skills can use an online generator/website to create a RAT and send it to people. They can be a type of virus that spreads easily like through email and unknowingly embedded into the side of some software. To learn more about a RAT and how to combat it, read on.
What is a RAT?
"RAT" is an acronym for remote access trojan. A RAT is as the name implies; It is a trojan that allows a hacker to have remote access to your computer. Many popular RAT generators allow you to quickly create an executable file. Imagine some malicious person sends the .exe file to someone and says, "I cracked this online game. Play it with me!". If the target opens it, the malicious person will easily be able to control their computer as it they were sitting in front of it. They can see a live stream of what is on the victim's screen, view the webcam of the computer, type onto the computer, and control the mouse. Some RAT software takes it a step further. RATs can allow a hacker to view the computer's files and download them without the real computer user seeing.
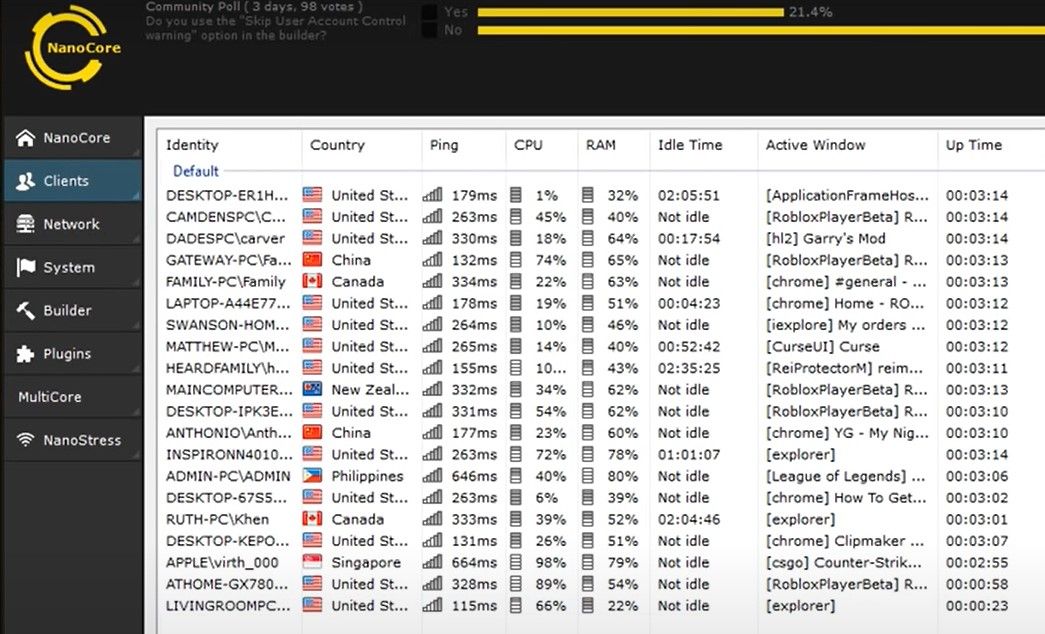
A RAT can work on most modern computers like Windows 10, Mac OS, Linux, and Android.
How do I get a RAT?
A RAT could be found everywhere. A RAT can be turned into a virus so it spreads easily to your friend's computer. A RAT can achieve this by modifying other files on your computer which you might send to other people. The same can be said with unknowingly infected friends sending one to you. If you're downloading hack software or cracked games, they might work as advertised, but they might also download malware at the same time. I would be extremely cautious when downloading .exe files.
How do I remove a RAT?
There is usually very little you can do to get rid of a RAT from your computer. If the RAT was created using a popular tool like Nanocore, you might be able to search on Google for a removal tool. Determining what the RAT was made with can be difficult and even a waste of your time. Using a RAT removal tool, in general, may be a waste of your time. This also goes to say for trying to use an anti-virus or any other kind of anti-malware tool to scan your computer for malicious content. Anti-malware programs are not always reliable and are easy to hide from when custom made.
If you need to get rid of any kind of malware from your computer, I always recommend plainly factory resetting your computer. Unless you're a highly educated computer engineer, you never truly know if a virus has already attached itself to other files. Again, anti-virus programs are not always reliable in detecting and removing such content.
Mitigating the risk of downloading a RAT
To best avoid downloading a RAT, you need to trust no-one. Only download content from big-time companies. Understand that any rogue teenager could create a fake website, fake emails, and malicious software like apps or bots. Anyone can achieve a high Google search result too. Relying on an anti-virus is not the smartest decision. If you're downloading from anywhere that isn't the official download page of a Fortune 500 company, check out these software to better protect yourself.

How do I know if I have a RAT?
A RAT can be incredibly difficult to spot if used by the hacker correctly.
- Check if any program you closed is still running in the background with the task manager. Hackers can hide from this easily. Most programs can be coded to hide from the Windows task manager.
- Watch your screen for movement. A hacker can send keyboard and mouse controls. Of course, a hacker will usually hide. They likely won't do it while you're at the computer. They can check if you're at the computer simply by looking at your webcam or by seeing if you're doing anything on the computer.
- Always monitor your internet activity. Occasionally check your internet activity logs as found on some websites like Facebook, Reddit, Google search, and banks. If logs show that activity is coming from your computer while you were not on it, this can suggest that your computer has a RAT.
- (This tip is more advanced) Monitor your internet activity using a network monitoring tool like Fiddler. If you're seeing that data is coming out from software you don't recognize or being sent to an IP/website/server you don't recognize, this could suggest that you're being live streamed or your file are being downloaded. It would be even smarter to monitor from your router/modem as well because a hacker likely has little to no access to it.
Hackers can hide simply by not doing anything to your computer. A hacker can instead just watch your screen and wait for you to go to websites containing sensitive information. Remember that they can also browse and download your files without you knowing even while you're using the computer.
Do not use this article for bad
I pretty much gave enough information to let you know how to make a RAT with Nanocore. If you want to experiment, please only test Nanocore on your spare computers. In doing so, you can better understand the potential and dangers of a RAT. Please do not use a RAT generator for malicious purposes. It is indecent, unethical, and illegal in most modernized countries
Summary
A remote access trojan is a type of malware that allows a hacker to get full control of a computer through the internet. A RAT allows the hacker to view the webcam, control the keyboard and mouse, and download files. Anyone with basic computer skills can use a RAT generator, so be careful when downloading files sent by random people or random websites.